Our idea on computer security has changed a lot in the recent years. When people thought of computer security, they thought about protecting the physical machine that contained important data. However, nowaday only the hardware is secure and the data is vulnerable to attacks. With each major technological advance in computing comes more security threats. Technology advances too fast for solutions to be developed. Therefore, developing security is just too difficult. The penetrator tries to find the holes while the designer tries to close them. The issue here is that we can never know if a system is perfectly secure, and that there is a likelihood that the penetrator will find a hole. Of course, with the appropriate techniques, the system can be built so it is highly unlikely to penetrate its security. BUT who prioritizes securitiy? When looking at a system, people often look at its price, functions, performance, reliability, compatibility, etc. Security will be at the bottom of the list! It may even just be a nuisance.
The bottom line is to protect yourself. The problem is not the computer, but THE PEOPLE. Download anti-virus programs to prevent your personal information from being stolen.
This blog is for the CS-100W class I am taking at SJSU and its purpose is to lay a foundation for a future career in Computer Science through professional writing.
Thursday, November 28, 2013
Sunday, November 24, 2013
Artificial Intelligence: Video Games
Can you think of a game without an AI or computer controlled opponent? I certainly can't! One of the most interesting fields of Computer Science is Artificial Intelligence, or known as AI. There are many applications for AI such as speech recognition (like Siri on iPhone), natural language processing, computer vision, etc. However, I find games are some of the more interesting applications that utilize AI. Well what is AI in games? They are techniques used to produce the illusion of intelligence in the behavior of non-player characters. You could have competent opponents or helpful allies!
How it is implemented depends on the type of game, such as RTS (Real-time strategy), FPS (First-Person shooter), RPGs, sport games, etc. Here are some common elements in which AI are implemented:
How it is implemented depends on the type of game, such as RTS (Real-time strategy), FPS (First-Person shooter), RPGs, sport games, etc. Here are some common elements in which AI are implemented:
- Event Driven Engine: AI reacts based on events.
- Specific AI Structure: how the AI moves and determines reasoning and its behavior.
- Path-Finding: finding the shortest path to a certain destination.
- Animation sequences for different body parts such as shooting/reloading in FPS.
- Scripted Behavior: show their personality through dialogue, contributing to the overall storyline of the game.
- Collision: detect obstacles in game.
As an SJSU student, I have yet to learn about the algorithms used in video games to create AI. The most popular algorithms used are A(*), Finite State machines, and Artificial Neural Networks. Every game you've played has definitely used some sort of AI, and have implemented these algorithms.
Sunday, November 17, 2013
History of Computer Science: Mobile Application Development
The history of mobile application development actually dates back to 2003, introduced first by IBM. It was not popular back then and only had basic features. However, a later major advancement arrived in 2002, when the Blackberry-smartphone was introduced. Thus began wireless emailing. As time went on, new mobile platforms(iOS and android) were introduced which further boosted mobile app development. With these smartphones, mobile technology became completely revolutionized. Mobile apps have allowed people to become more efficient and allow new experiences. For me, I have used the Udemy app which allows me to take a course anywhere, without the need for laptop or desktop.
Sunday, November 10, 2013
File Sharing: Client-Server Downloading vs. P2P Sharing
I’m sure you have downloaded something off the web but do
you know the process? When you download
something, your computer, the client, tells the server (computer that holds the
web page and file) to transfer a copy of the file to your computer. This transfer goes through a protocol, or set
of rules. The transfer speed is affected by the type of protocol (FTP or HTTP),
amount of traffic on server, and number of other users downloading the
file. How does this traditional
client-server download contrast with peer-to-peer sharing?

 In peer-to-peer sharing, you use a software program, such as
BitTorrent. BitTorrent downloads
torrents, which are files that point to the computer with the desired file.
BitTorrent sends a request for the file by communicating with a tracker
(central server with the file) to locate other computers connected to the
internet. The tracker finds a swarm, or
a group of connected computers that are file sharing. Once BitTorrent finds a seeder, or a computer
that has the complete file, it will start downloading the file. Basically, you are downloading small bits of
files from different sources at the same time.
Once you finish downloading, you
will become a seeder and help others download the file.
In peer-to-peer sharing, you use a software program, such as
BitTorrent. BitTorrent downloads
torrents, which are files that point to the computer with the desired file.
BitTorrent sends a request for the file by communicating with a tracker
(central server with the file) to locate other computers connected to the
internet. The tracker finds a swarm, or
a group of connected computers that are file sharing. Once BitTorrent finds a seeder, or a computer
that has the complete file, it will start downloading the file. Basically, you are downloading small bits of
files from different sources at the same time.
Once you finish downloading, you
will become a seeder and help others download the file. BitTorrent is sometimes used for distributing copyrighted material but the program is still legal. If you choose to download any copyrighted material, you are at risk of being caught, since the download can be traced back to you. Be careful and happy downloading!
Sunday, November 3, 2013
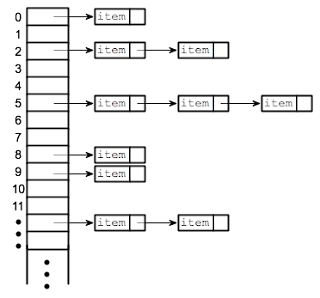
Data Structures: Real World Applications
If you’re a CS major, I am sure you have come across a data
structure. You may have worked with
arrays, linked lists, graphs, or trees.
These are all ways of storing and organizing data for efficient usage. There
is no “best” data structure and are used depending on the task at hand; all data structures have pros/cons. The question is HOW are these structures used
in the real world? Let’s take a look at a few common ones:
1) Linked List
1) Linked List
An example on how a linked list may be used in the real world is managing a train. These trains are linked together in a calculated way so that items can be loaded, transferred, unloaded, and picked up efficiently. Like a linked list, trains can be added or removed at any point of the train. Also, the train at the end can be removed easier than the train in the middle. Therefore, one may use a linked list in order to plan the order of the trains, and the contents of the trains.
2) Binary Search Trees
Binary Search Trees are often used for data that is constantly added or removed, such as a map or set of objects. For example, any language library (C++, Java, .Net, etc) uses binary search to find items; items are inserted in order, and items can be easily accessed.
3) Hash Tables
Internet Routers use Hash Tables; a router table may contain millions of entries. Therefore, the router must determine the best route by querying the router table when the packet is routed to a specific IP address. In this case, the key is the IP address and the value is the address.
Knowing when to implement these data structures is important because some are more efficient, depending on the task!
Subscribe to:
Comments (Atom)