Artificial Neural Networks are computational models that are capable of machine learning and pattern recognition. They were inspired by the animal central nervous system. Today, they are used in many fields and have been well-established in any discipline, especially medicine. They can extract information from raw data and then build computer models for medical decision-making.
Now you know what they are capable of doing but what exactly are they? They are basically systems of connected neurons that compute values from inputs by pushing information through the network. According to the Wiley Online Library, these models contain computing nodes that operate as nonlinear summing devices. The nodes are interconnected by weighted connection lines, and the weights are adjusted when data are presented to the network. If successfully trained, the artificial neural networks can perform tasks such as classifying an object, predicting an outcome value, recognizing a pattern, and completing a known pattern.
Since applications of artificial neural networks serve such broad spectrum of fields, they help validate research in those areas. For example, medical decision support in medical applications. These networks must be understood thoroughly before being used. Check out this list in which neural networks have been successfully applied.
This blog is for the CS-100W class I am taking at SJSU and its purpose is to lay a foundation for a future career in Computer Science through professional writing.
Monday, December 9, 2013
Monday, December 2, 2013
Computer Graphics: Computer-generated Imagery
Have you seen the latest Ender's game movie? No!? What are you doing reading this post then? In most movies like Ender's game, computer-generated imagery (CGI) is used. It is an application of Computer Science (commonly referred to 3D graphics) to create special effects in films, television shows, simulators, commercials, etc. Content is able to be produced without the use of extra props, and expensive set pieces. The real question is how are these special effects done? There are a few steps to incorporate CGI into a film:
- Modeling
- Animation
- Rendering
- Compositing
The first step is for an artist to create the images the director wants by the use of clay models, photographs, or drawings. This could be the hybrid human-alien race in the movie Avatar in which actors take the place of them.
The second step starts when the model is perfected. The animator tells the computer how the model moves. An example of this could be how the Transformers move or how their face moves when they talk.
The next step is for a renderer (program that contains lighting, texture, shading, and more features) to create images showing the moving 3D models. The director modifies the lighting and materials, often doing so until it looks perfect.
The next step is for a renderer (program that contains lighting, texture, shading, and more features) to create images showing the moving 3D models. The director modifies the lighting and materials, often doing so until it looks perfect.
Lastly, the CG images are combined with the live-action part using compositing software.
Thursday, November 28, 2013
Communications and Security: Computer Security
Our idea on computer security has changed a lot in the recent years. When people thought of computer security, they thought about protecting the physical machine that contained important data. However, nowaday only the hardware is secure and the data is vulnerable to attacks. With each major technological advance in computing comes more security threats. Technology advances too fast for solutions to be developed. Therefore, developing security is just too difficult. The penetrator tries to find the holes while the designer tries to close them. The issue here is that we can never know if a system is perfectly secure, and that there is a likelihood that the penetrator will find a hole. Of course, with the appropriate techniques, the system can be built so it is highly unlikely to penetrate its security. BUT who prioritizes securitiy? When looking at a system, people often look at its price, functions, performance, reliability, compatibility, etc. Security will be at the bottom of the list! It may even just be a nuisance.
The bottom line is to protect yourself. The problem is not the computer, but THE PEOPLE. Download anti-virus programs to prevent your personal information from being stolen.
The bottom line is to protect yourself. The problem is not the computer, but THE PEOPLE. Download anti-virus programs to prevent your personal information from being stolen.
Sunday, November 24, 2013
Artificial Intelligence: Video Games
Can you think of a game without an AI or computer controlled opponent? I certainly can't! One of the most interesting fields of Computer Science is Artificial Intelligence, or known as AI. There are many applications for AI such as speech recognition (like Siri on iPhone), natural language processing, computer vision, etc. However, I find games are some of the more interesting applications that utilize AI. Well what is AI in games? They are techniques used to produce the illusion of intelligence in the behavior of non-player characters. You could have competent opponents or helpful allies!
How it is implemented depends on the type of game, such as RTS (Real-time strategy), FPS (First-Person shooter), RPGs, sport games, etc. Here are some common elements in which AI are implemented:
How it is implemented depends on the type of game, such as RTS (Real-time strategy), FPS (First-Person shooter), RPGs, sport games, etc. Here are some common elements in which AI are implemented:
- Event Driven Engine: AI reacts based on events.
- Specific AI Structure: how the AI moves and determines reasoning and its behavior.
- Path-Finding: finding the shortest path to a certain destination.
- Animation sequences for different body parts such as shooting/reloading in FPS.
- Scripted Behavior: show their personality through dialogue, contributing to the overall storyline of the game.
- Collision: detect obstacles in game.
As an SJSU student, I have yet to learn about the algorithms used in video games to create AI. The most popular algorithms used are A(*), Finite State machines, and Artificial Neural Networks. Every game you've played has definitely used some sort of AI, and have implemented these algorithms.
Sunday, November 17, 2013
History of Computer Science: Mobile Application Development
The history of mobile application development actually dates back to 2003, introduced first by IBM. It was not popular back then and only had basic features. However, a later major advancement arrived in 2002, when the Blackberry-smartphone was introduced. Thus began wireless emailing. As time went on, new mobile platforms(iOS and android) were introduced which further boosted mobile app development. With these smartphones, mobile technology became completely revolutionized. Mobile apps have allowed people to become more efficient and allow new experiences. For me, I have used the Udemy app which allows me to take a course anywhere, without the need for laptop or desktop.
Sunday, November 10, 2013
File Sharing: Client-Server Downloading vs. P2P Sharing
I’m sure you have downloaded something off the web but do
you know the process? When you download
something, your computer, the client, tells the server (computer that holds the
web page and file) to transfer a copy of the file to your computer. This transfer goes through a protocol, or set
of rules. The transfer speed is affected by the type of protocol (FTP or HTTP),
amount of traffic on server, and number of other users downloading the
file. How does this traditional
client-server download contrast with peer-to-peer sharing?

 In peer-to-peer sharing, you use a software program, such as
BitTorrent. BitTorrent downloads
torrents, which are files that point to the computer with the desired file.
BitTorrent sends a request for the file by communicating with a tracker
(central server with the file) to locate other computers connected to the
internet. The tracker finds a swarm, or
a group of connected computers that are file sharing. Once BitTorrent finds a seeder, or a computer
that has the complete file, it will start downloading the file. Basically, you are downloading small bits of
files from different sources at the same time.
Once you finish downloading, you
will become a seeder and help others download the file.
In peer-to-peer sharing, you use a software program, such as
BitTorrent. BitTorrent downloads
torrents, which are files that point to the computer with the desired file.
BitTorrent sends a request for the file by communicating with a tracker
(central server with the file) to locate other computers connected to the
internet. The tracker finds a swarm, or
a group of connected computers that are file sharing. Once BitTorrent finds a seeder, or a computer
that has the complete file, it will start downloading the file. Basically, you are downloading small bits of
files from different sources at the same time.
Once you finish downloading, you
will become a seeder and help others download the file. BitTorrent is sometimes used for distributing copyrighted material but the program is still legal. If you choose to download any copyrighted material, you are at risk of being caught, since the download can be traced back to you. Be careful and happy downloading!
Sunday, November 3, 2013
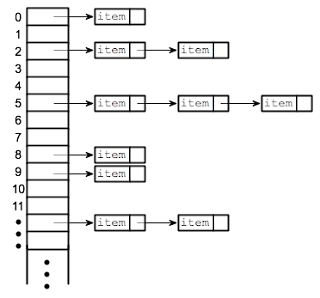
Data Structures: Real World Applications
If you’re a CS major, I am sure you have come across a data
structure. You may have worked with
arrays, linked lists, graphs, or trees.
These are all ways of storing and organizing data for efficient usage. There
is no “best” data structure and are used depending on the task at hand; all data structures have pros/cons. The question is HOW are these structures used
in the real world? Let’s take a look at a few common ones:
1) Linked List
1) Linked List
An example on how a linked list may be used in the real world is managing a train. These trains are linked together in a calculated way so that items can be loaded, transferred, unloaded, and picked up efficiently. Like a linked list, trains can be added or removed at any point of the train. Also, the train at the end can be removed easier than the train in the middle. Therefore, one may use a linked list in order to plan the order of the trains, and the contents of the trains.
2) Binary Search Trees
Binary Search Trees are often used for data that is constantly added or removed, such as a map or set of objects. For example, any language library (C++, Java, .Net, etc) uses binary search to find items; items are inserted in order, and items can be easily accessed.
3) Hash Tables
Internet Routers use Hash Tables; a router table may contain millions of entries. Therefore, the router must determine the best route by querying the router table when the packet is routed to a specific IP address. In this case, the key is the IP address and the value is the address.
Knowing when to implement these data structures is important because some are more efficient, depending on the task!
Sunday, October 27, 2013
Hacking: iOS Jailbreaking
Jailbreaking is the legal process of bypassing restrictions
on Apple devices (iPhone, iPad, iPod Touch) running the iOS system. If you
want to know how it exactly works, an explanation on how the evasi0n jailbreak
works is shown here.
Essentially, what happens is a modified set of kernel
patches is installed. The kernel is the supervisor of the OS and allows you to
run unsigned code. When you jailbreak,
you’re able to use unauthorized software and download tweaks. However, there is a reason why Apple made the
iOS to be a closed environment! Let’s go over some pros/cons.
Pros
Pros
- New apps. Apps like Cydia allow you to install apps that are not in the Itunes App Store.
- Customization. Winterboard allows you to change your icons and wallpaper, customize sounds, etc.
- Secure Shell Client (SSH). You can manage all of your iPhone’s files.
Cons
- No security and limited antivirus protection. You never know if the unauthorized app you are downloading contains malware.
- Instable; can brick your phone and render it useless.
- No warranty.
If you decide to jailbreak your phone, do it at your own
risk! If you are careful in what you download, you can maximize the true
potential of your device. I have
jailbroken my iphone (iOS 6) and have downloaded some useful apps myself. TheiOS 7 jailbreak is not released yet so
sit tight. If you do happen to jailbreak
your phone, check out these.
- Nitrous: significantly speeds up web browsing on mobile device
- BiteSMS: quicker way to compose/reply to messages.
- MapsOpener: forces map links to open in Google Maps instead of stock Apple Maps app.
For me, jailbreaking my iphone has allowed me to take advantage of unauthorized but useful apps. I highly recommend anybody to jailbreak to make the best use of the device. Just remember to be careful!
Sunday, October 13, 2013
Open Source: Free Tools
 Everything comes with a price. Except free open source software! Open source refers to something that can be modified because its design is publicly accessed. Therefore, open source software is software whose source code is available for modification by anyone. You may have heard of Firefox, Thunderbird, Open Office, BitTorent, VLC Media Player, Audacity, etc. These are all FREE tools that everyone should take advantage of! Here is my favorite open source software list:
Everything comes with a price. Except free open source software! Open source refers to something that can be modified because its design is publicly accessed. Therefore, open source software is software whose source code is available for modification by anyone. You may have heard of Firefox, Thunderbird, Open Office, BitTorent, VLC Media Player, Audacity, etc. These are all FREE tools that everyone should take advantage of! Here is my favorite open source software list:1) Open Office: This is a great alternative to Microsoft Office that handles most of Microsoft Office's productivity tasks from document production to creating full multi-media presentations.
2) VLC Media Player: very simple and powerful media player since it can play most codecs (MPEG-2, DivX, H.254, MKV, WebM, WMW, MP3..)., plays everything (files, discs, webcams...) and runs on all platforms (Windows, Linux, Mac OS X...).
3) Audacity: a multiplatform audio edittor that can import and export in numerous formats (WAV, FLAC, AU...). It is useful for anyone that needs to manipulate audio.
Of course there's benefits of being a consumer of these tools but what about on the developing side?
Public collaboration. Most open source projects, like Wordpress, are created by a large number of programmers, all working together to create a software package. Also, because it's open source, source code is available to ALL developers that want to contribute.
Go take advantage of these free tools!
Sunday, October 6, 2013
Agile: Understanding Agile Methodology
When I first heard of agile in my CS100W class, I was thinking of the actual definition: Characterized by quickness, lightness, and ease of movement. I continued to learn that the term "agile" in class refers to a software development method! You may have heard of other software development methods such as Waterfall, Spiral, Iterative and Incremental, etc. These are all methods that work as a framework which controls project development and maintenance. Agile Methodology is an alternative to traditional project management, based on iterative and incremental development. Requirements and solutions through cooperation between self-organizing, cross-functional teams.
Here are some underlying principles of Agile Methodology:
1) Complex projects are broken into smaller, attainable goals.
2) Simplicity
3) Face to face communication (the best kind of communication!)
4) Close, daily cooperation between business people and developers
5) Regular adaption to changing circumstances
A framework that uses agile methodology is Scrum. Projects are broken down into smaller pieces that are managed and completed in short intervals called sprints. These sprints, which are often two to four weeks, involve short term goals that are part of the main goal. Following the process above, customers receive the "Release" often and are able to evaluate it so that modifications can be made.
Agile is a very powerful tool that can be used efficiently in any project. Although it may not be the best option, it provides a productive approach for teams and product development.
Friday, September 20, 2013
LinkedIn and Branding: Expand Your Network
Are you looking for a job? Yes? No? In either case, you NEED LinkedIn. Why? LinkedIn is basically a social networking website that is all about NETWORKING. Having connections is the key to your SUCCESS. LinkedIn helps you expand your professional network and increase your chances of being found and evaluated. Nowadays, employers have been increasingly using LinkedIn to seek talent by conducting background research, sourcing candidates, and acquiring references. But what if you already have a job and you're not looking one? It doesn't matter. 80% of users on LinkedIn are currently not seeking employment. By having a large network, you can use it in case you are laid off and then have a higher chance to be employed again. If you are seeking employment, 77% of all job openings are posted on LinkedIn! You are missing out on many opportunities of landing a job by not having a profile. Once you make a profile and put yourself out in the world, you allow employers to connect with you, even if you're not log in all the time.
So maybe you have a LinkedIn account already but are you utilizing it to its fullest? The most important thing is having a very strong and complete profile. To make a great impression, you need to fill it out to increase your chances of being offered a job. You are your own brand and you need to advertise your professional resume. You want to show WHY people should hire YOU. Start building your Network today!
 |
| Expand your network |
Friday, September 13, 2013
QR Codes: What are they and how do they work?
 |
| Created using Quickmark |
You see that weird looking square on the left side there? If you have a smart phone, download the QR code reader app if you haven't already and scan it. Well what is it!? That's right, it is direct link to my blog! How does it do that? That square is called a QR code, which is basically a two-dimensional bar code that stores information. You are already familiar with the 1-dimensional bar code, which you've seen at grocery stores. Bar codes are stored only in its horizontal widths and its spaces while its vertical makes no difference.
 |
| Sample barcode taken from http://freebarcodefonts.dobsonsw.com/ |
.jpg) |
| A poster used in Japan made by Disney to allow people to access exclusive information |
Friday, September 6, 2013
Pros/Cons of Social Networking
- Maintain connections and create closer bonds.
- Allows job employment by letting businesses to reach out to potential employees.
- Find others who share same interest.
- Increase overall quality of life by communication among friends.
- a platform for communication between professors and students that promotes education.
- Allow businesses to promote their brand.
Cons:
- Lack of privacy, allowing intrusions of government.
- Can lead to stress due to conflicting relationships or having no companionship.
- Discourages people to make physical interactions.
- Dissemination of false information.
- Easily allows people to waste time.
- Negative publicity for a business's brand.
Despite these pros and cons, an important aspect of social networking is its security. Anyone using any kind of social media is at risk because of hacks, and viruses. Confidential information could be stolen. Tech companies such as Facebook, Microsoft, NBC, and New York times have been hacked! The latest hacks involve the victim to visiting "infected pages" first and result in computers allowing hackers access to the network's private information. It is no doubt that these hacks will ever stop so be cautious whenever using social networking sites!
Friday, August 30, 2013
Welcome!
Welcome Professor Caires and my fellow peers!
My expertise in Computer Science:
As a senior at San Jose State University, I have not
discovered my expertise in computer science yet. Having taken courses that teach Java, windows
programming, and C, I am still learning many things about the field and have
not found my specialty. However, I hope
to specialize in a field that relates to my passion for games, such as game programming.
 |
| Final Fantasy XIV: A Realm Reborm |
What I find exciting about Computer Science:
Computer science is always growing and has limitless opportunities to impact aspects of everyday life. For any area there will always be some application of computer technology. The thought that I could create any application I want excites me and motivates me to pursue this career. I could be part of a video game developing company, helping to program the best role playing game of all time. Or I could create a program that allows robots to perform surgery in hospitals. Or I could work with a company that does Mobile Application Development, building e-commerce apps. The opportunities are endless and I like that freedom. Although it’s very challenging, that’s what makes it exciting. There are always new skills to learn, problems to solve, and applications to create. What I’m particularly interested in the Computer Science field is video game design. I want to know HOW my favorite games are all made, and how I can contribute to that field. I want to be part of the development of a worldwide known game.
Computer science is always growing and has limitless opportunities to impact aspects of everyday life. For any area there will always be some application of computer technology. The thought that I could create any application I want excites me and motivates me to pursue this career. I could be part of a video game developing company, helping to program the best role playing game of all time. Or I could create a program that allows robots to perform surgery in hospitals. Or I could work with a company that does Mobile Application Development, building e-commerce apps. The opportunities are endless and I like that freedom. Although it’s very challenging, that’s what makes it exciting. There are always new skills to learn, problems to solve, and applications to create. What I’m particularly interested in the Computer Science field is video game design. I want to know HOW my favorite games are all made, and how I can contribute to that field. I want to be part of the development of a worldwide known game.
 |
| Screenshot of Final Fantasy XIV |
Challenges I believe I can tackle with what I know as a Computer Scientist:
With my knowledge and developed problem-solving skills, I believe I can tackle real world problems. Since I'm working in the IT department at U.S. Merchant Systems, a credit-card processing company, I've worked with real data from merchants (our customers) and have learned to manage a database using Visual Studio and C#. Of course, I'm still learning so I have the potential to address other difficult problems.
With my knowledge and developed problem-solving skills, I believe I can tackle real world problems. Since I'm working in the IT department at U.S. Merchant Systems, a credit-card processing company, I've worked with real data from merchants (our customers) and have learned to manage a database using Visual Studio and C#. Of course, I'm still learning so I have the potential to address other difficult problems.
Subscribe to:
Comments (Atom)